This blog is about how to deploy a SCEP certificate connector for Microsoft Intune. The example shows the SCEP connector and the SCEP profile to deploy certificates.
This blog is based on this blog from Saurabh Sarkar. I have used his blog to build my variant on the implementation and I want to share this with you. For example, the installer for the Intune Certificate Connector and the Intune interface itself has changed. My PKI environment is based on Windows Server 2022 which makes the screenshots more up-to-date.
The deployment has a couple of steps:
- Create the certificate template
- Install the NDES role
- Install the Intune certificate connector
- Install the Azure AD Application Proxy
- Create the SCEP profiles in Intune
Prerequisites
There are some prerequisites to this blog.
- Existing PKI environment.
- Intune Admin with a license (to log on to the certificate connector)
- Access to Application Proxy with Azure AD
- Create a Service Account to run the NDES role (Logon as Service, Issue and Manage Certificates on the CA, Read and Enroll permissions on the template, Permission to the KSP, Full Details)
Create the SCEP Certificate Intune Template
Firstly, log on to your subordinate certificate authority to create the template.
After that, right-click on certificate templates and click on manage
Next, look for the User template and click duplicate:

Fill in the variables for all the tabs listed below:
Set the Template Name. Don’t use spaces, things are easier if you don’t.

Check whether the extensions are correct:

Make sure the Subject Name is supplied within the request:

In addition, we need to set up the Key usage also. Select Key Usage and click edit:
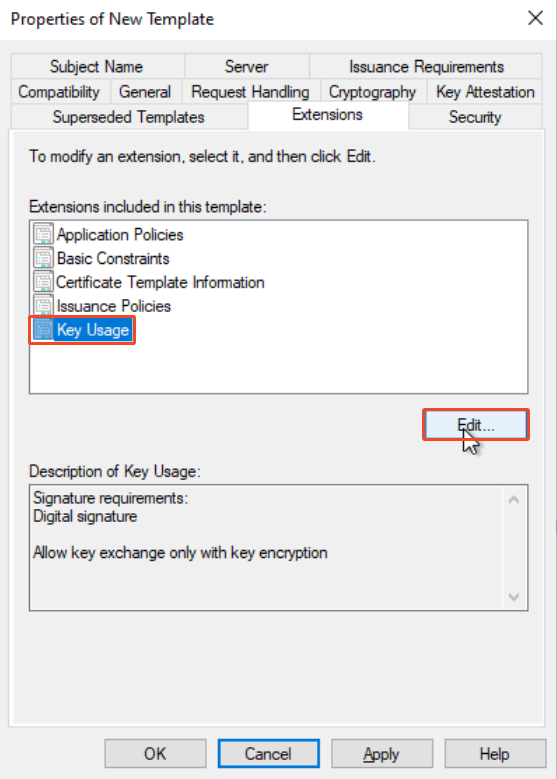
After that, make sure these boxes are checked:
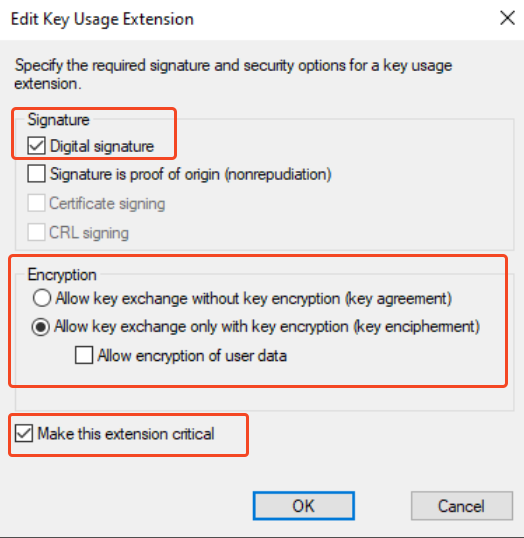
Make sure to add the computer name that is going to host the NDES role.
And add the Service Account that runs the NDES role from the prerequisites.

Set the Cryptography settings:

After that, we have the new template:

Lastly, we need to issue the template:
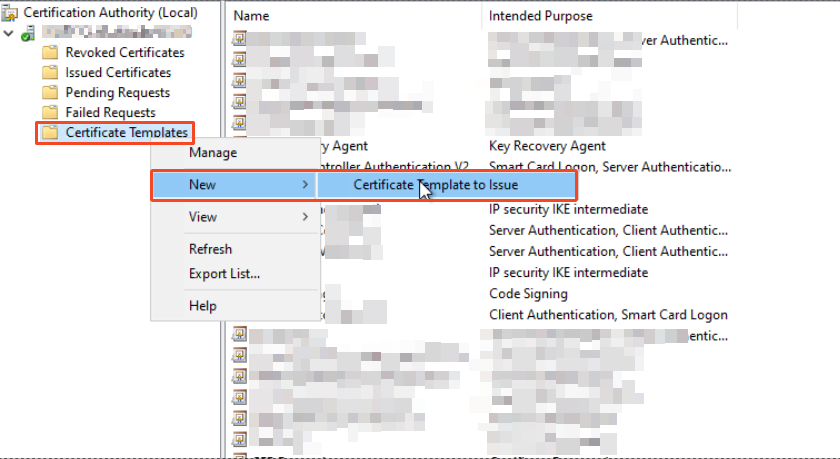
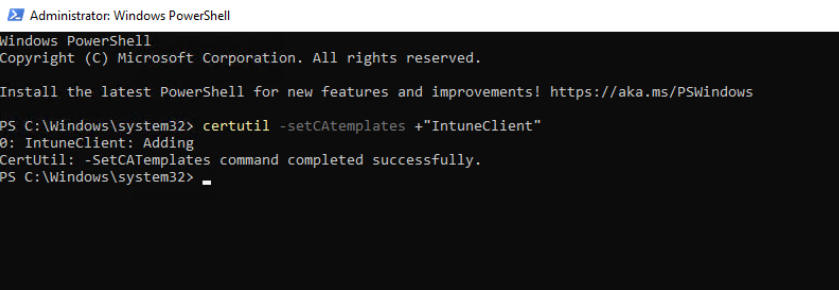
In addition, you can also do this by using this command:
certutil -setCAtemplates +"IntuneClient"
Install NDES Role
Firstly, we need to add the Service Account to this group:
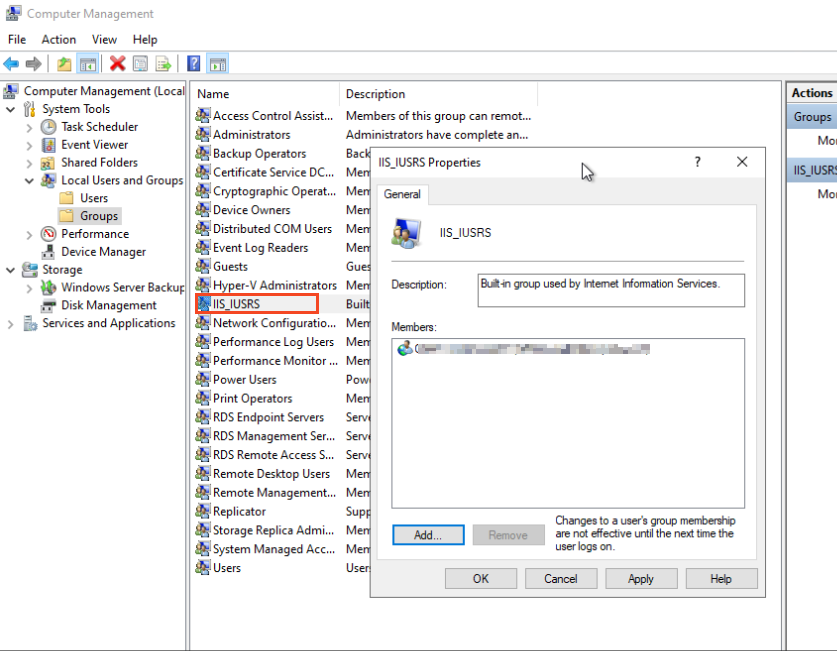
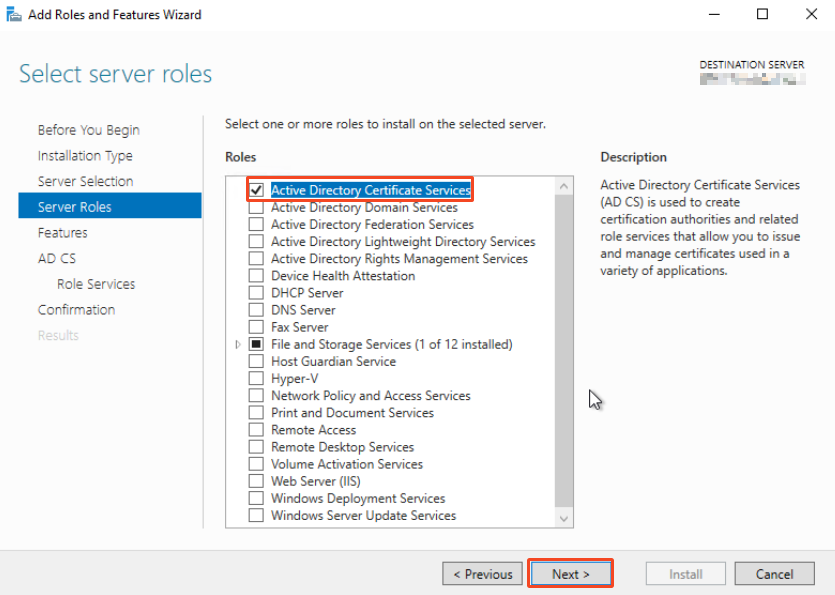
Log on to the server and click on Add roles and features. Click through the first pages until you see this window:
Select this role and click next:
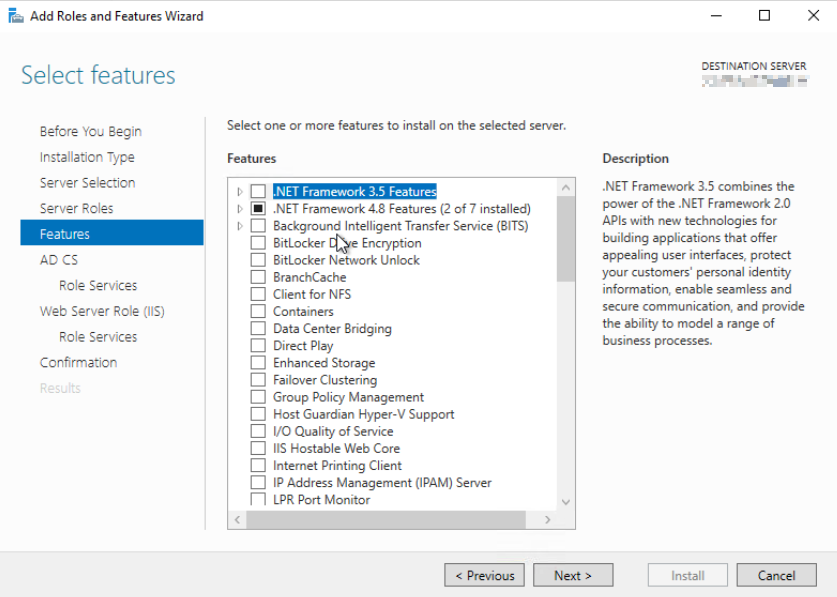
At the features window:
Make sure to select:
Web Server > Security > Request Filtering
Web Server > Application Development > ASP3.5 and ASP 4.5
IIS 6 WMI Compatibility
It is not in the screenshot.
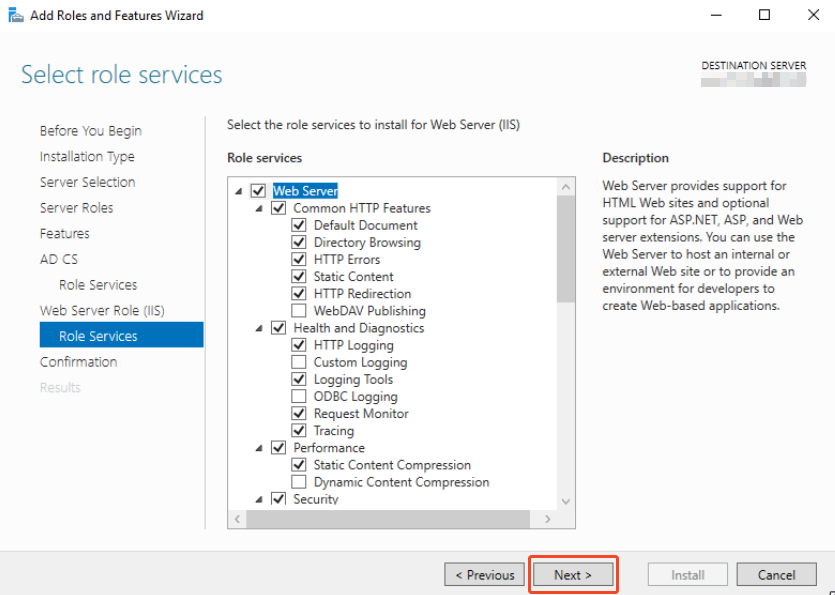
Click next:

Select this role:

Make sure to select:
Web Server > Security > Request Filtering
Web Server > Application Development > ASP3.5 and ASP 4.5
It is not in the screenshot.
Lastly, click on Configure and after that, Click on “Configure Active Directory Certificate Services on the Destination Server”

Specify the admin credentials. This must be an Enterprise Administrator

After that, select the role to configure:

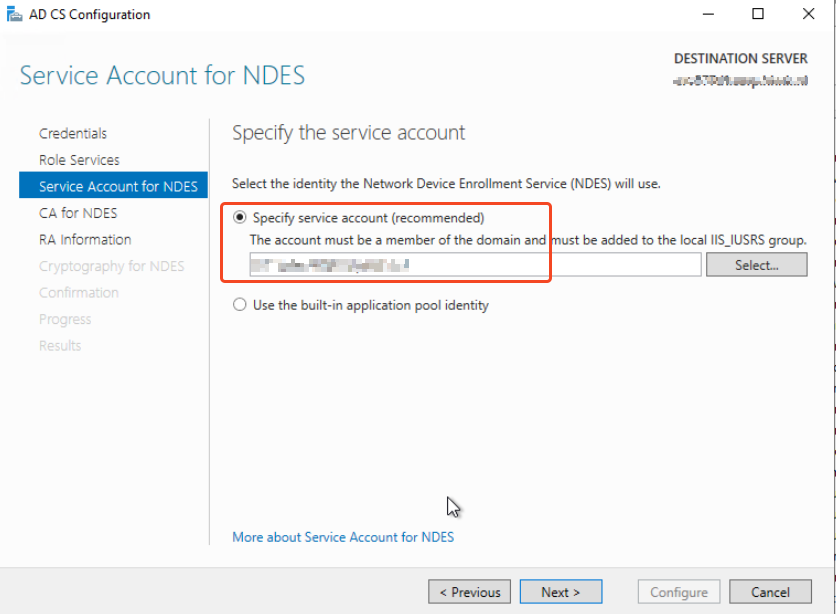
Specify the service account:
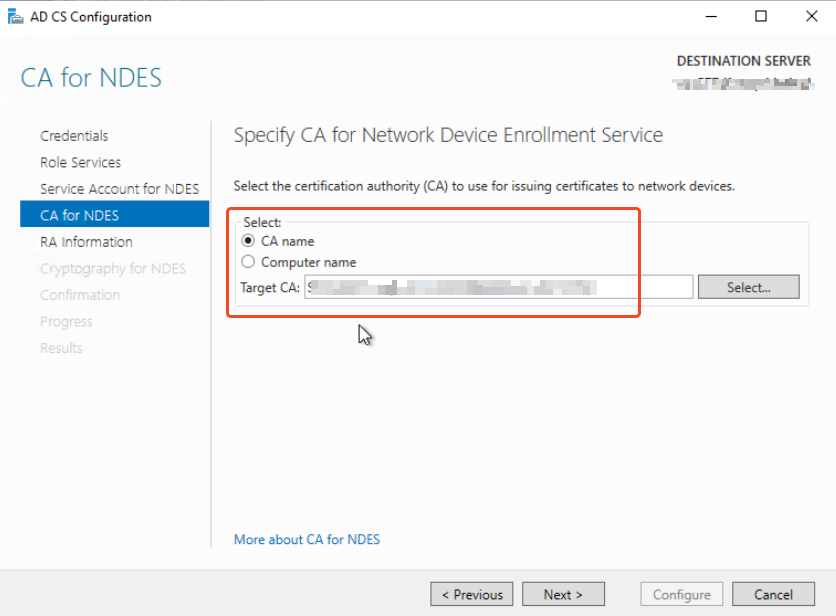
After that, specify your issuing CA:
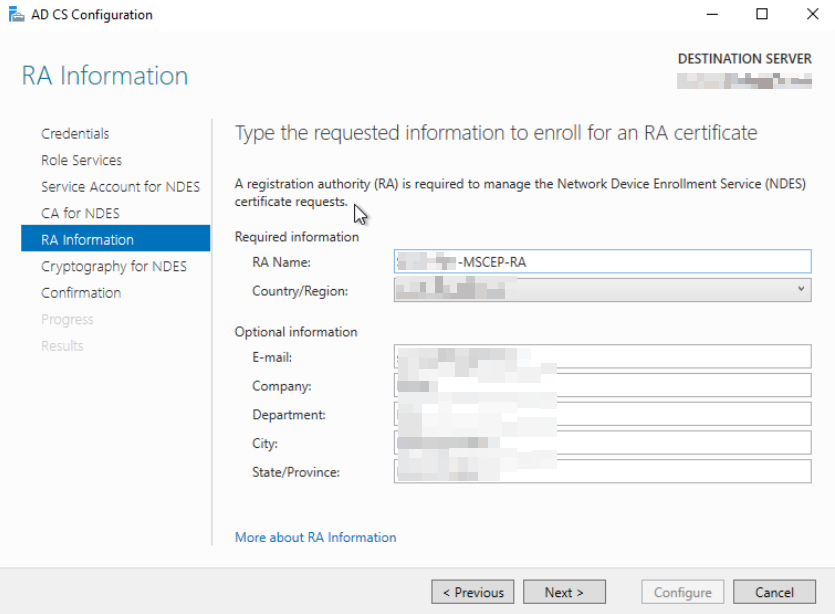
Set the information for the RA certificate:
Set the key lengths:

And configure:

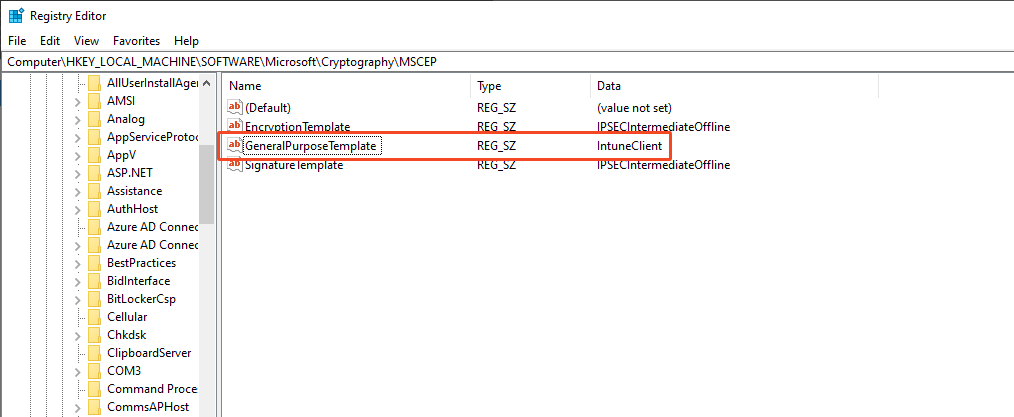
Check the registry if the correct template is set. If not, set this accordingly:
In addition, this is what you see in IIS after installation:
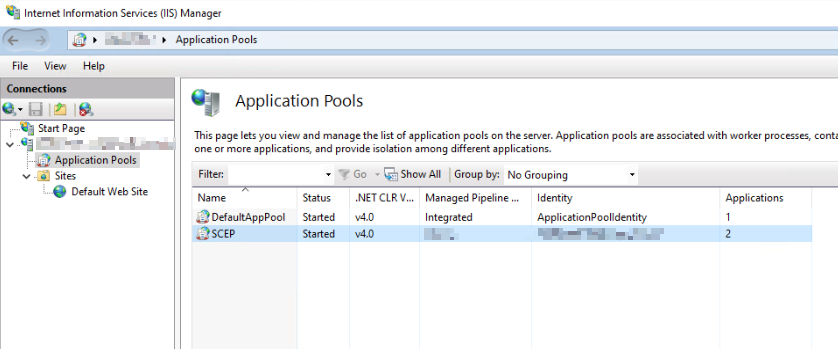
And in the certificate manager:
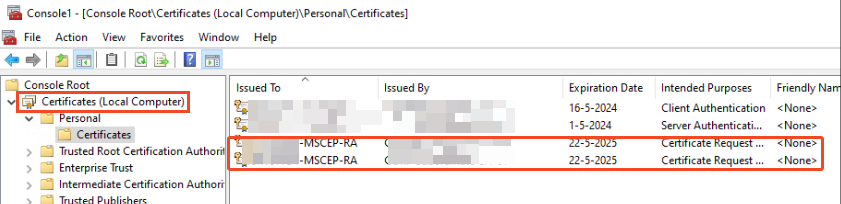
After that we need to edit the IIS binding to use the server certificate so it can use HTTPS:
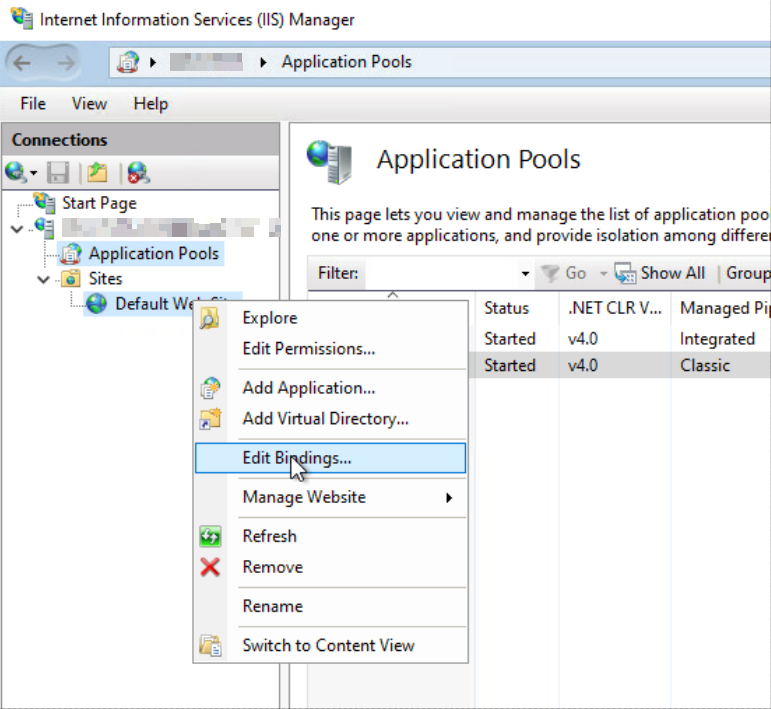
Select the certificate:
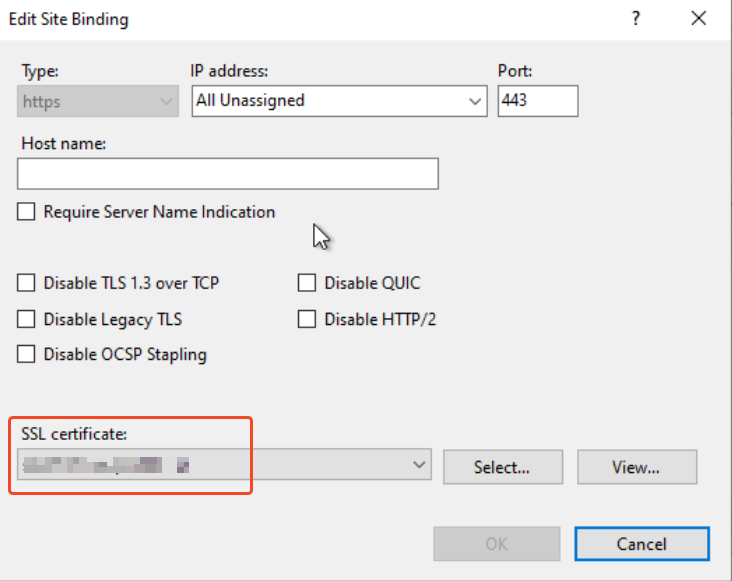
In addition, you could add a hostname also. If you like.
Next, make sure your NDES server is available: (by going to the URL of your server)
This should be the result:
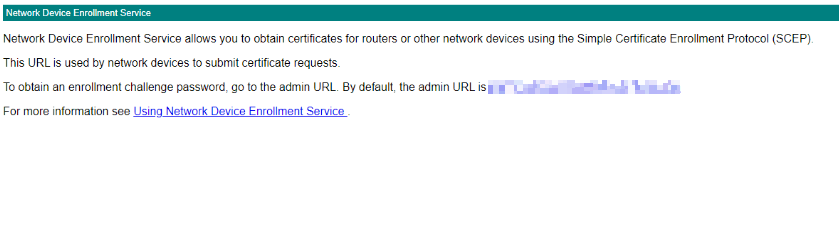
Furthermore, if you access the service via the SCEP URL, this should be the result:
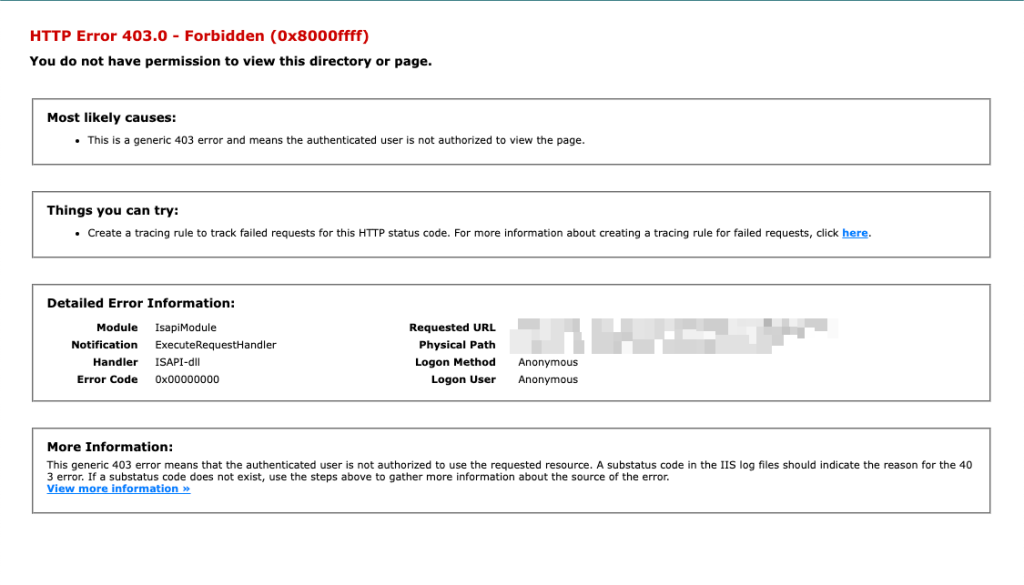
This request is only allow when you have an Intune Managed Device with a SCEP request.
Install the Intune Certificate Connector
Firstly, download the Intune Certificate Connector from your Tenant:
After that install the Certificate Connector as ADMINISTRATOR (Very important)

After that, we need to configure the connector. This is the first window shown:
Click next:

Select the features you want to disable or enable:
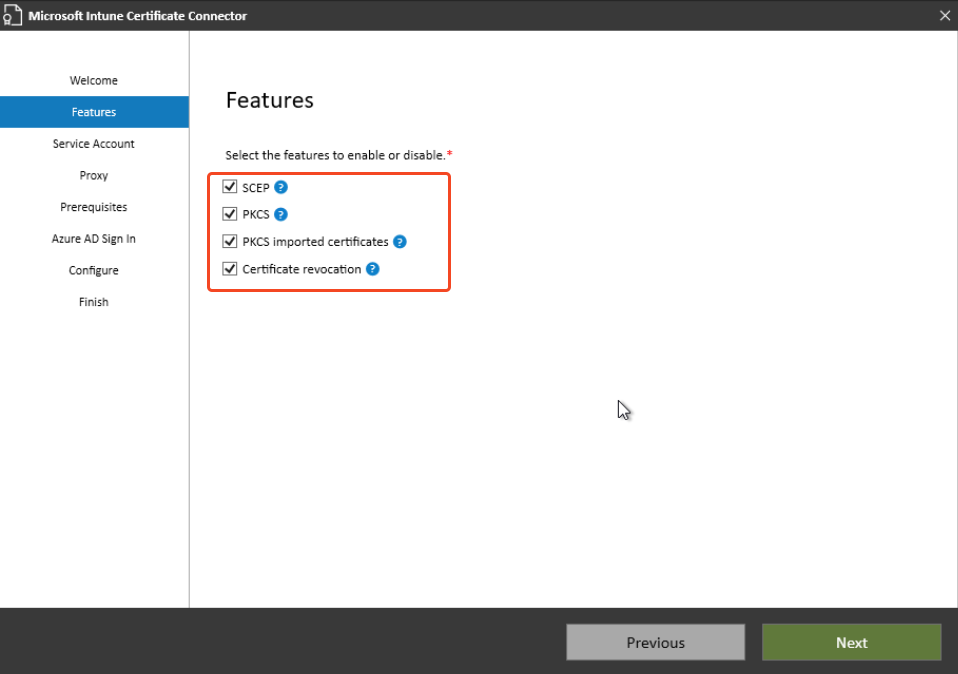
Enter the service account:

Enter the proxy settings, if any:

It should breeze past the Prerequisites:

A browser window opens asking you to log on to Azure AD:

Lastly, click configure:
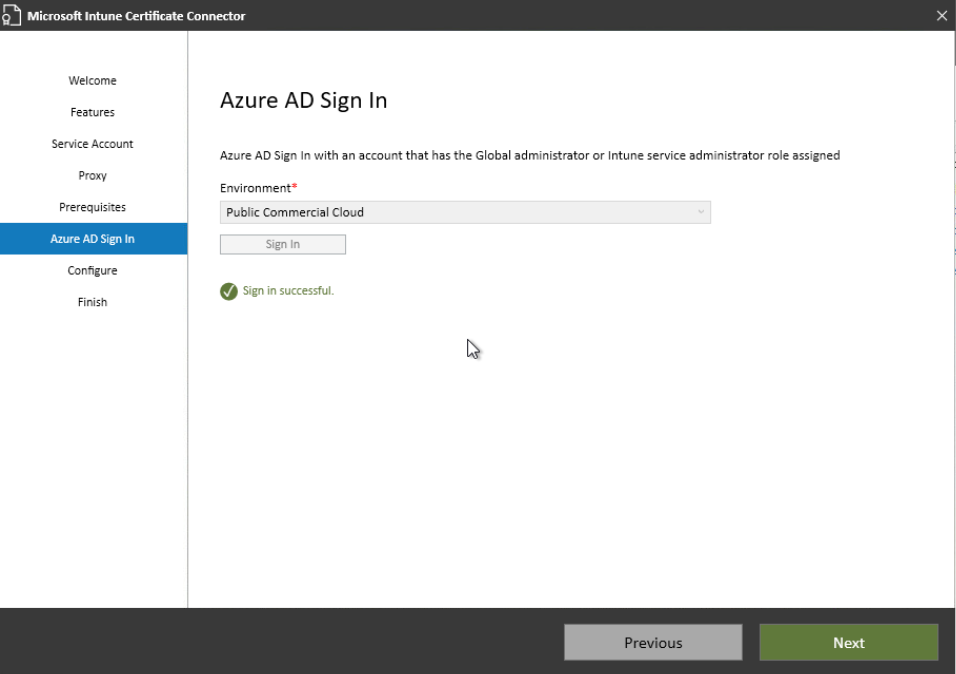
After that, the connector is configured:

After that, this certificate is available:
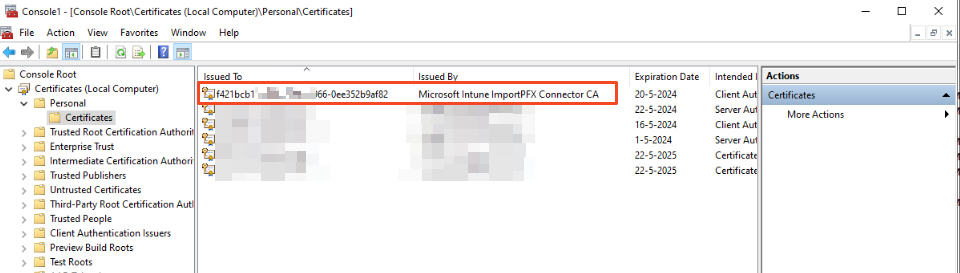
Install Azure AD Application proxy
Firstly, log on to Azure AD and go to Application Proxy.
I created a new connector group called Intune PKI Connector:

After that, download the connector service and install it on the server that hosts the NDES role:

It will then become active in the connector group:

After that, click Configure an app:

Enter the appropriate URLs and connector groups:

You need the external URL in order to configure the SCEP profile in Intune.
Configure the Intune SCEP profiles
Firstly, you need to create a profile for your Root Certificate and your Intermediate Certificate.
Do this twice: (Once for Root, Once for Intermediate)
So, click on create profile > Platform: Windows 10 and later > Profile Type: Templates > Template name: Trusted Certificate.
Enter a name.
After that, upload the trusted certificate:
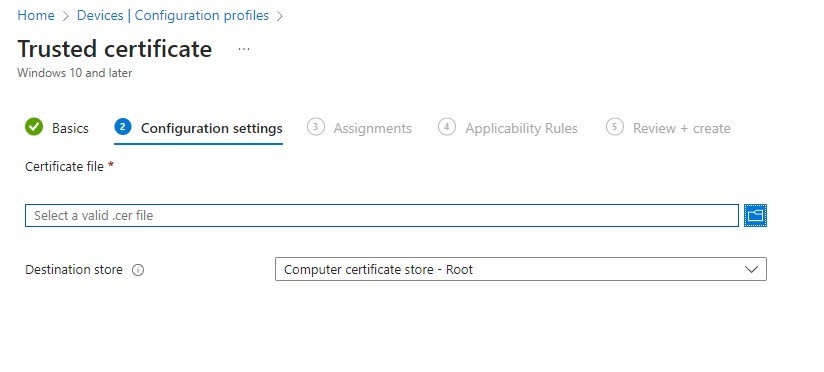
Assign the policy and that’s that.
Lastly, we need to create the SCEP profile (finally)
So, click on create profile > Platform: Windows 10 and later > Profile Type: Templates > Template name: SCEP Certificate.
Enter a name.
Configure the profile like this:
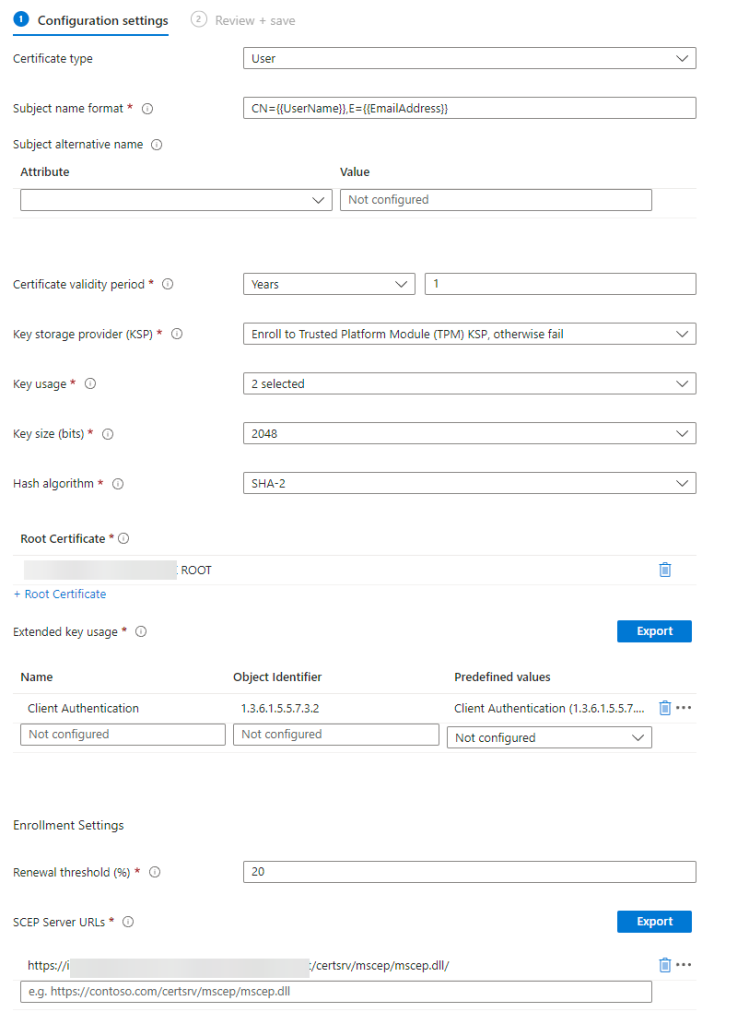
And after that, you are able to deploy a SCEP Certificate via the Intune Connector!
Result:

Thanks for reading!
The Error message is:
Failed to add the following certificate templates to the enterprise Ative Directory Certificate Services or update security settings on those templates:
EnrollmentAgentOffline
CEPEncryption
IPSEC (Offline request)
Element not found. 0x80070490 (WIN32: 1168 ERROR_NOT_FOUND)
Hi,
Did you add the Service Account to the prerequisites posted at the top of the blog? That is very important. Otherwise, It will not work.
Thanks,
Niels
Just curious is the SCEP website needs to be available public or internal only works fine because of the Intune connector ?
Hi Tabish,
That depends on your environment. The device that is about to enrolled in Intune needs to be able to access the SCEP url. You can choose yourself if that is public or not.
Thanks,
Niels