This is a blogpost about setting Bitlocker drive encryption for WVD sessionhosts in an Azure DevOps Release Pipeline. The Bitlocker key will be stored in an Azure Keyvault. This post is only about the script you use to automatically enable Bitlocker on your VM’s. Dishan Francis created an excellent post about creating a Key Vault and Key to use for Bitlocker drive encryption. I will reference this post in the prerequisites.
Prerequisites
Firstly and most importantly set up Azure Key vault according to this blog:
Dishan Francis’s blog about setting up Azure Key Vault
Secondly, it is required that you already have setup your Azure DevOps Release Pipeline to deploy Windows Virtual Desktop Hostpools.
Script Syntax
$installedPackageProvider = Get-PackageProvider
if ($installedPackageProvider.Name -notmatch "NuGet") {
Install-PackageProvider -Name NuGet -force
Write-Host("Install powershell module NuGet")
}
$installedModules = Get-InstalledModule
if ($installedModules.Name -notmatch "Az.Accounts") {
Install-Module Az.Accounts -Force -AllowClobber
Write-Host("Install powershell module Az Accounts")
}
$installedModules = Get-InstalledModule
if ($installedModules.Name -notmatch "Az.Compute") {
Install-Module Az.Compute -Force -AllowClobber
Write-Host("Install powershell module Az Compute")
}
Write-Host("assignment value ")
$secret = ConvertTo-SecureString -String "SECRET" -AsPlainText -Force
$username = "APP ID"
Write-Host("setting up credential")
$Credential = New-Object -TypeName "System.Management.Automation.PSCredential" -ArgumentList $username, $secret
Write-Host("connect......")
Connect-AzAccount -Credential $Credential -Tenant "AZURETENANTID" -ServicePrincipal
Select-AzSubscription -SubscriptionId "SUBSCRIPTION ID" | Set-AzContext
$ResourceGroupName = RESOURCEGROUPNAME
$KeyvaultResourceID = KEYVAULTRESOURCEID
$KeyID = KEYID
$KeyvaultURI = KEYVAULTURL
$VMsToEncrypt = Get-AzResource -ResourceGroupName $ResourceGroupName | Where-Object ResourceType -eq Microsoft.Compute/virtualMachines
foreach ($VM in $VMsToEncrypt){
Set-AzVMDiskEncryptionExtension -ResourceGroupName $ResourceGroupName -VMName $VM.Name -DiskEncryptionKeyVaultUrl $KeyvaultURI -DiskEncryptionKeyVaultId $KeyvaultResourceID -KeyEncryptionKeyUrl $KeyID -KeyEncryptionKeyVaultId $KeyvaultResourceID -Force
}
Azure DevOps implementation
If you have read previous posts then the following will look familiar.
Firstly, logon to your Azure DevOps organization and go to your release pipeline.
Secondly, edit the release pipeline. You see the following:

Click on the task you want to add the bitlocker encryption script to. For example “HostPool Dev”:

Next, add a new task:

Lookup “Azure CLI” and add the task:

Name the task, select you ARM Connection, choose the Powershell as Script Type and copy the script from the Script syntax chapter to the Inline Script section:

Take in account that you need to edit the variables in the script. For example: “RESOURCEGROUPNAME”.
Now run the release pipeline. You should see this result in the task for the Bitlocker Drive Encryption section:

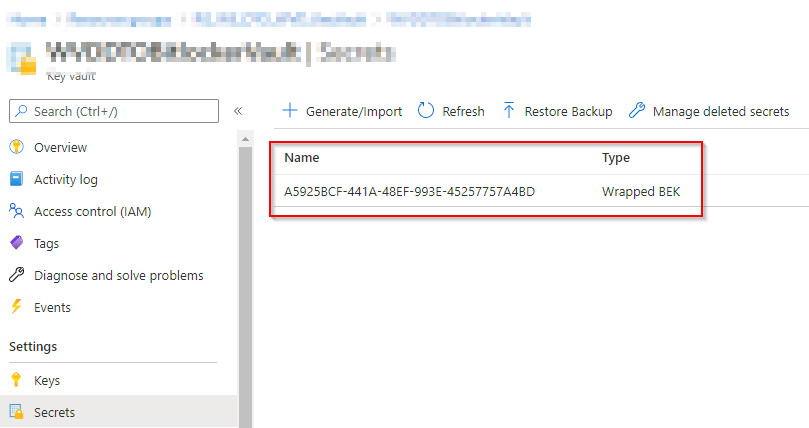
This is the view from the Azure Key Vault perspective:

After that, you have automated your Bitlocker drive encryption for WVD Session hosts via an Azure DevOps Release Pipeline.
References
Dishan Francis’s blog about setting up Azure Key Vault
Other WVD posts:
Token Refresh Script for Azure DevOps Release Pipeline
Flow Triggered DevOps Build
3 thoughts on “Bitlocker encryption Azure DevOps Release Pipeline”