Lately, I am playing around with Microsoft Defender for Endpoint and how to add an exclusion in Attack Surface Reduction.
Let’s first walk through the situation at hand. I am building a new Microsoft Endpoint Manager solution for a customer of mine and they use a custom-made signature module (Signature365/Innovative365). This custom module didn’t work at first:
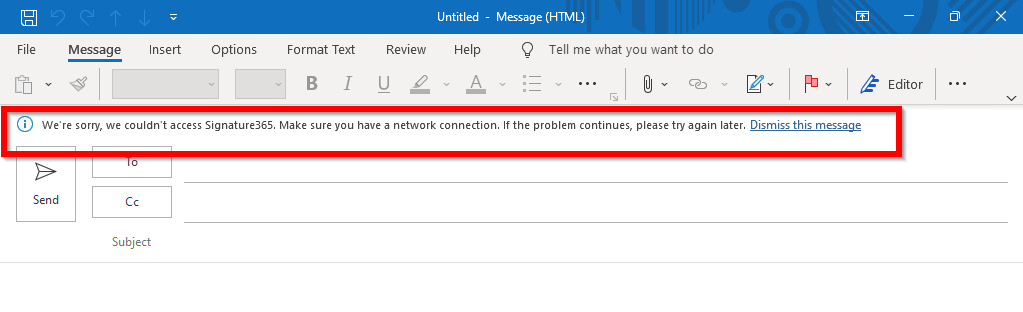
Detection of the blocked app
I had enabled the Microsoft Security baseline for Windows 10 and the one for Microsoft Defender for Endpoint. It turned out that these rules were blocking the custom module. Firstly, I opened the Windows Security Center. This didn’t give me a lot of information:
Only a “Risky Action blocked” notice without further information.
Since we use Microsoft Defender for Endpoint I decided to give that portal a chance. So I logged on to https://security.microsoft.com/ and go to Endpoints and Configuration Management:
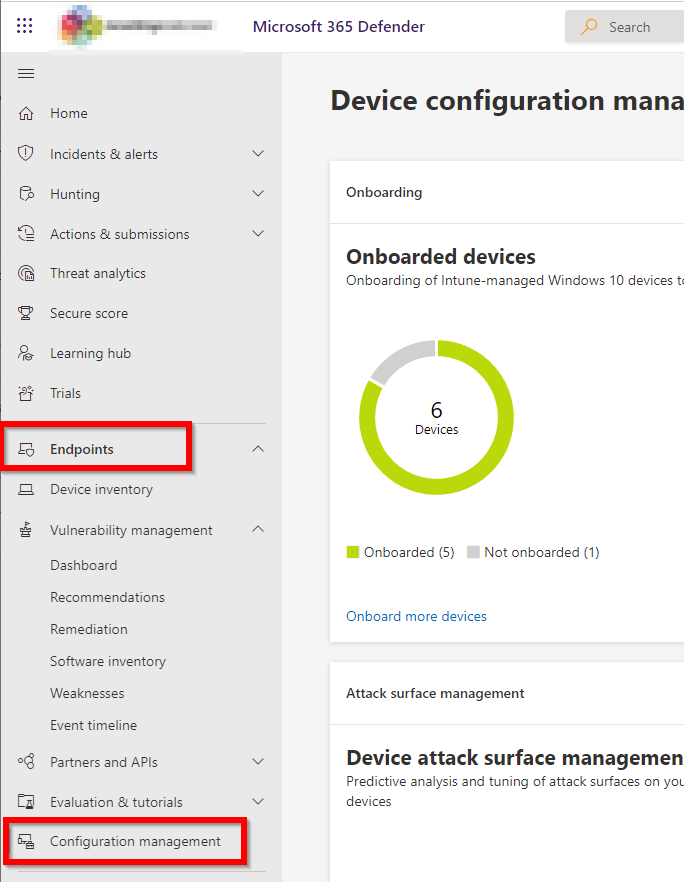
After that, I selected “Attack Surface Management”:
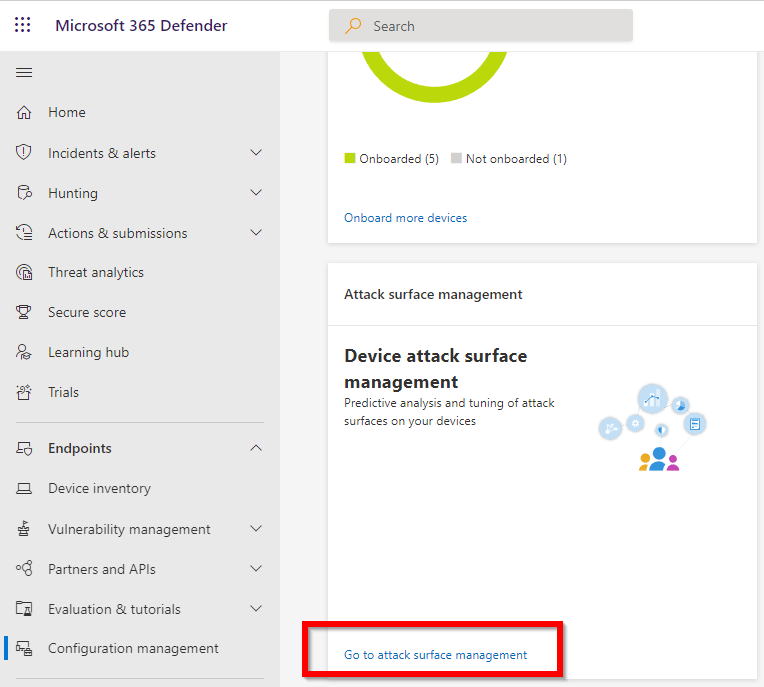
This immediately shows the detection that is made by Defender:
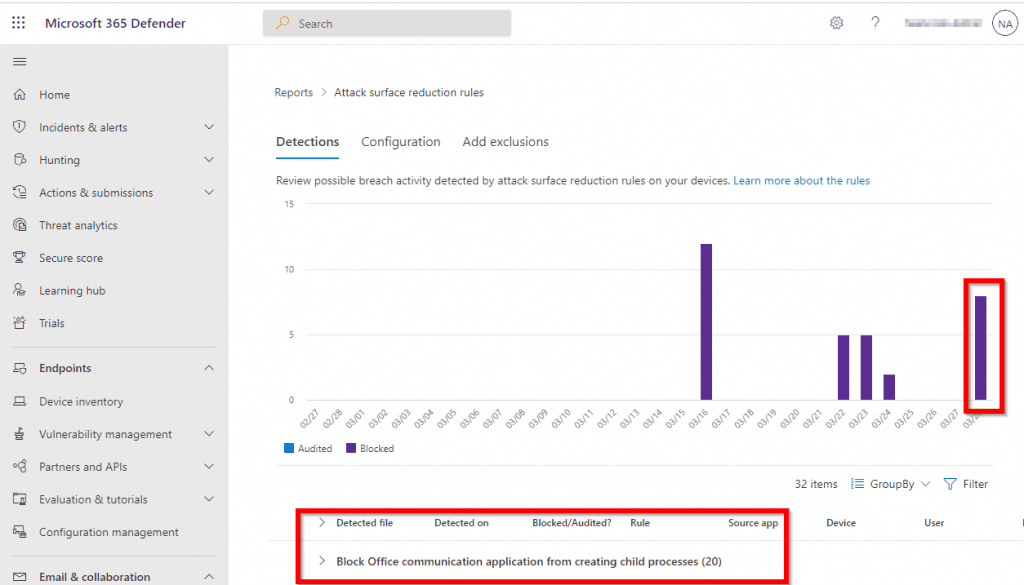
The detection is really clear. It states a blocked child process. It seems like exactly what I’m looking for.
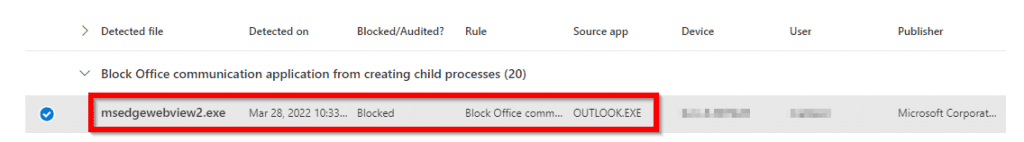
When you further drill down on the detection, it shows the application, date and time, and source app of the detection:
Add the Exclusion
After that, you click on “Add Exclusions”:
Select the application you want to exclude and click on “Add Exclusion or Get exclusion details”:
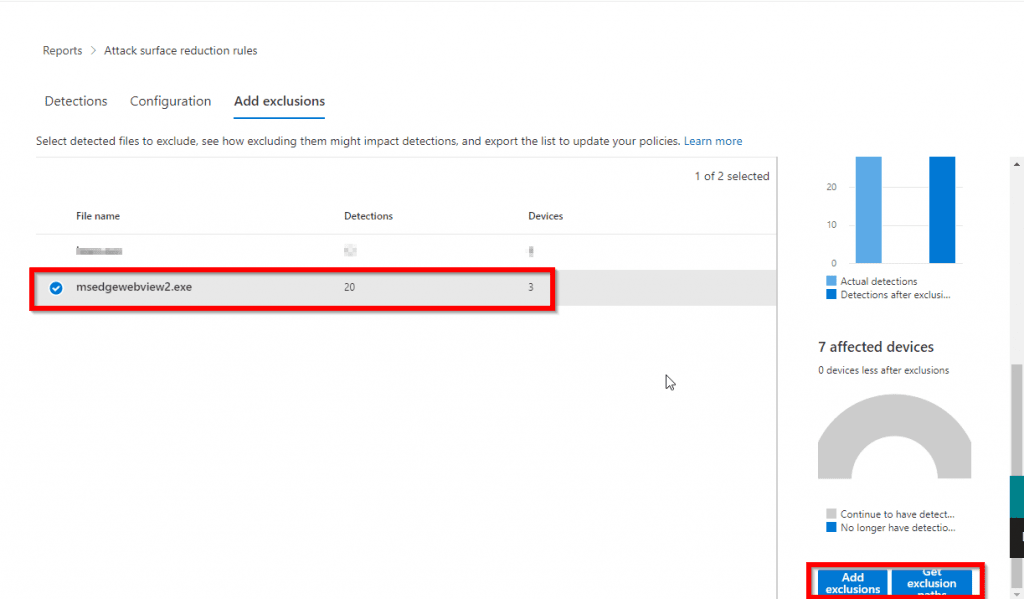
The “Add Exclusions” button takes you right to Microsoft Defender for Endpoint > Attack Surface Reduction Profiles.
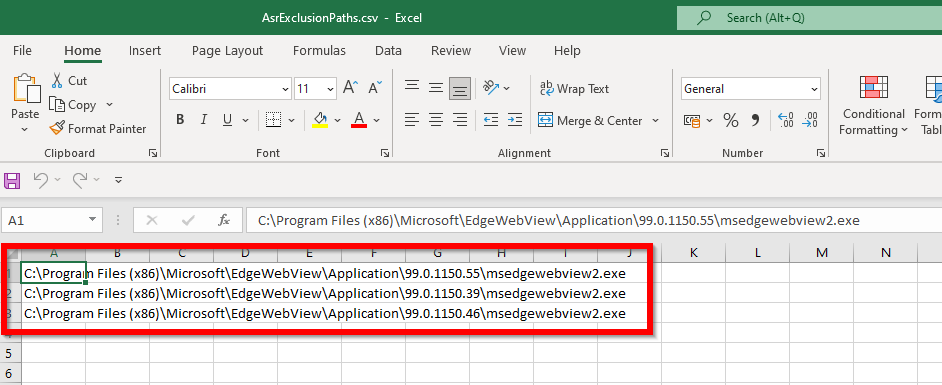
The “Get Exclusion Paths” button downloads a CSV file with the paths you need to exclude.
For example:
NOTE: If you already had the attack surface reduction configured via the Security Baselines (Windows 10 & Microsoft Defender for Endpoint), like me :-)… You can’t add exclusion to the Attack Surface Reduction configuration. You are only able to configure these settings:
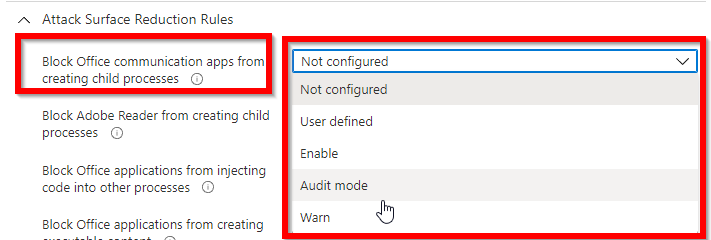
That is not good enough for us. We just want to exclude our specific case.
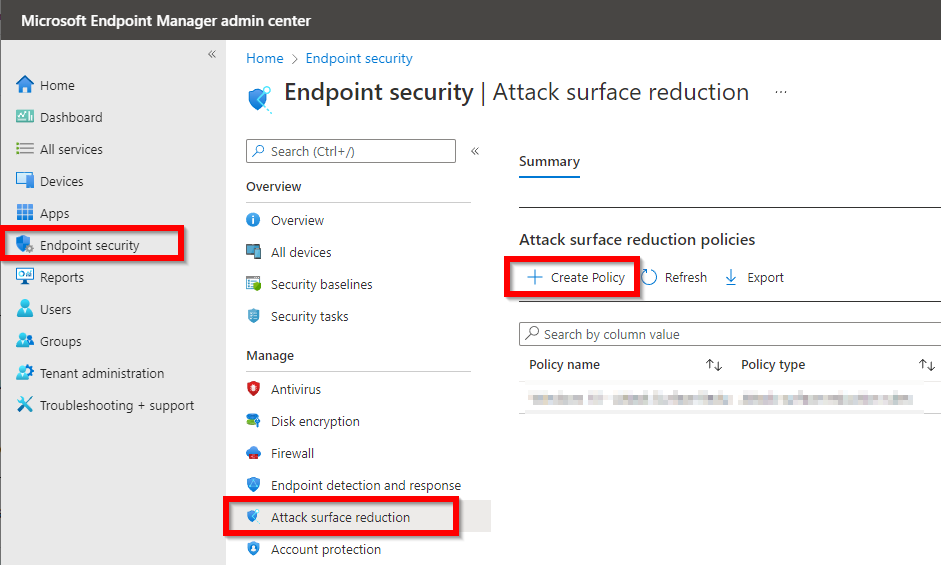
So, if you have the baselines configured with Attack Surface Reduction rules. Please set these to not configured and create a new Attack Surface Reduction policy.
If you don’t use the baselines, please just create a new Attack Surface Reduction Policy:
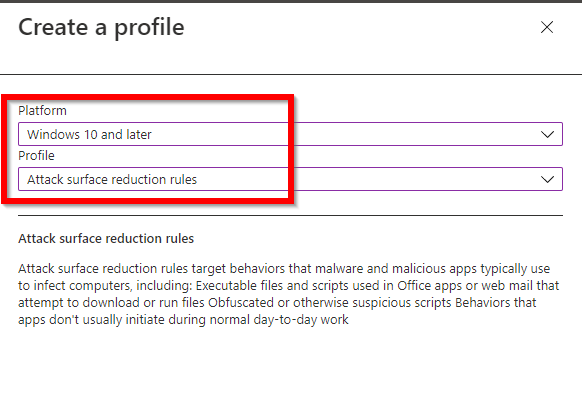
Name the policy and go to configuration settings. After that, set all the configuration you need and scroll down to the exclusion part:
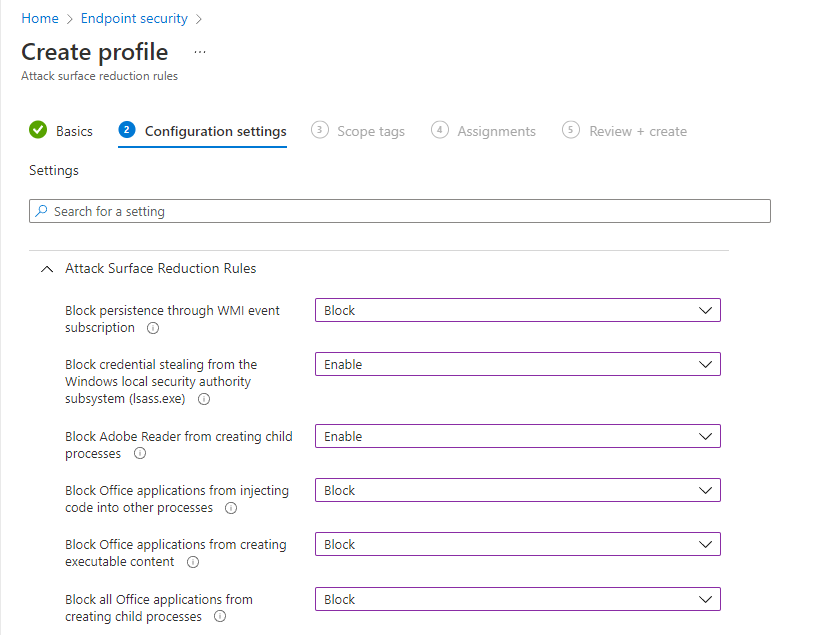
Add all the exclusions from the CSV file:
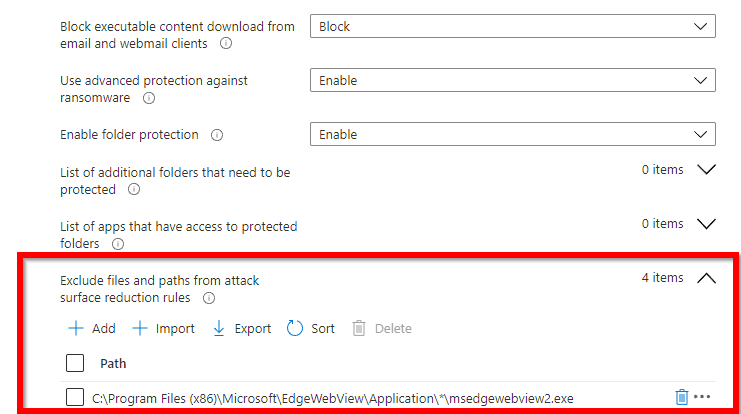
The wildcard you see is for the version number in Microsoft Edge. This way this is excluded for future versions.
That’s how you add an exclusion!
Other posts:
Elevate Administrative Tools on an Endpoint managed device
Packer YAML series
Great post & thanks for sharing. It’s important to note that the exclusion instructions are for the older style Attack Surface Reduction (ASR) policies, not the newer ones Microsoft introduced in early 2023. Instead of a global exclusion, you’ll have to add your exclusions to the specific Attack Surface Reduction (ASR) rule, which in this case is “Block Office communication application from creating child processes.”
Hi Julius,
That is completely true. I need to update this one if I find the time. 🙂
Thanks,
Niels